Managing Security Threats
The how-to guide for managing security threats including accessing incident report details, understanding costs and how to make improvements.
Managing Security Threats
When managing an Incident Report, you can review the information previously submitted through the Supervisor Portal. You also have the capability of adding important details to the report. A Security Threat report has additional questions on the Report Management page that add valuable information to the report.
-png.png)
Accessing Incident Report Details
From the Report Management menu, the second tile from the left will be labeled Incident Report. On this tile, you will see the name of the person that submitted the report and their job title. Under this information you will see INCOMPLETE. Once the report has been closed, this will change to COMPLETE. For more information on closing a report, click here
-png.png)
To see the report details and to add information, click the Incident Report tile. The details of the report will appear on the right of the page.
Managing Security Threat Reports
The first portion of the Incident report will display information that was submitted in the original report. If the report included a security threat incident, you will see the heading Security within the Incident report summary. Below this heading, you will see the information that has already been submitted for the report.
At the end of the previously completed section, you will see a series of questions to answer. If a question is not applicable, leave it blank.
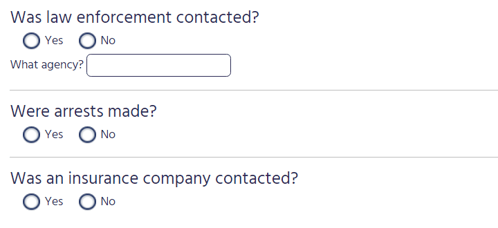
Was law enforcement contacted?
Depending on if law enforcement was contacted, click either Yes or No. If you select Yes:
- Click on the textbox next to What agency? and type the name of the law enforcement agency that was contacted.
Were arrests made?
Depending on if an arrest was made, click either Yes or No.
Was an insurance company contacted?
Depending on if an insurance company was contacted, click either Yes or No.
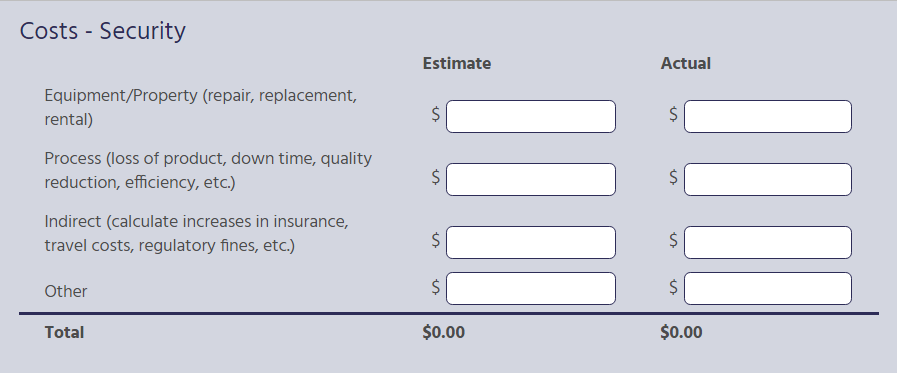
 Costs – Security
Costs – Security
In this section, you can enter both the estimated and actual costs associated with the security threat, if any. You can enter costs for the following categories:
- Equipment/Property (repair, replacement, rental)
- Process (loss of product, downtime, quality reduction, efficiency, etc.)
- Indirect (calculate increases in insurance, travel costs, regulatory fines, etc.)
- Other
For each line item that has a cost, click on the blank text box next to $ and enter the amount using your computer’s numerical keyboard. If there is no cost associated with a line item, you can leave it blank. The totals for each category will appear at the bottom of each column for both estimated and actual costs.
Suggested Improvements
The initial Incident Report will have a section for suggested improvements which you can review here.
Saving Reports
Once all questions have been reviewed and completed, click Save.
Printing Reports
To print the Close Call Report, click the printer icon at the top right-hand corner of this page and then follow your computer’s printing instructions.
Editing Reports
To edit any portion of the report that was originally submitted in the initial report:
- Click on the edit icon found at the top left-hand corner of this page.
- Once changes have been made, click Save at the bottom of the page.
- To exit editing mode without saving changes, click the “X” at the top-right corner of the report. A pop-up window will appear, “Do you want to save the report?”
- Click Yes to save your changes or No to not save your changes.
Additional Questions for Other Types of Incidences
If other types of incidences were selected in the initial report, additional questions may be generated on this page to review and complete.
For more information on managing the different types of Incidence Reports, click the links below.
(Link to Managing Motor Vehicle Reports)
